No matter what's going on around us, the internet keeps us in touch and spending time with our favorite people. This week will focus on staying safe while being social.
1. While we keep in touch online, it is important to avoid phishing scams. Phishing attacks use email or malicious websites to infect your machine with malware and viruses to collect personal and financial information. Cybercriminals attempt to lure users to click on a link or open an attachment that infects their computers, creating vulnerabilities for criminals to use to attack. Phishing emails may appear to come from a real financial institution, e-commerce site, government agency, or any other service, business, or individual. The email may also request personal information such as account numbers, passwords, or Social Insurance numbers. When users respond with the information or click on a link, attackers use it to access users’ accounts. As the AU Community, we need to avoid phishing scams while we are learning and working online .
2. It is also important to keep private information private.The Internet touches almost all aspects of the daily lives of the AU Community. In addition to learning and working, we are able shop, bank, connect with family and friends, and handle our medical records all online. These activities require you to provide personally identifiable information (PII) such as your name, date of birth, account numbers, passwords, and location information. It is important to take extra caution when we receive requests to provide PII online.
3. Using strong passphrases and complex passwords and enabling multi-factor authentication (MFA). Creating a strong password is a critical step to protecting yourself online. Using long, complex and unique passwords is one of the easiest ways to defend yourself from cybercrime. No one is immune to cyber risk. With numerous long,complex and unique passwords comes the need for a password manager. Have you noticed how often security breaches, stolen data, and identity theft are consistently front-page news these days? Perhaps you, or someone you know, are a victim of cyber criminals who stole personal information, banking credentials, or more. As these incidents become more prevalent, you should consider using multi-factor authentication, also called strong authentication, or two-factor authentication. Many institutions today require both a password and one of the following to log in: a call, email, biometric scan or text containing a code. By applying these principles of verification to more of your personal accounts, such as email, social media, and more, you can better secure your information and identity online!
We’re not always able to be around for the big things in life, but the internet has made it easier to share in those moments even when we can’t be there in person. From the video of your baby’s first steps to photos of their graduation, this week will focus on sharing special moments safely.
1. Wait until you get back: Posting pictures while you enjoy your vacation or special event could alert criminals that you are away from home and sometimes give away your location. Maintain your digital bliss and wait until you return home to post your photos.
2. Actively manage location services: Whether your vacation takes you to an exotic beach resort or on an action-packed adventure, location tools come in handy while planning your getaway or navigating a new place. Keep in mind that they can also expose your location through photos. Turn off location services when not in use.
3. Back it up: Capture and save the precious memories from your pre-nuptial party photos, the ceremony, reception and honeymoon to a secure cloud site or an external hard drive where they can be stored safely.
4. Secure video conferencing: Sometimes you want to stream your special moment so that your friends and family can join from different geographical locations. Ensure that you secure these video conferences by using passwords to avoid intruders (zoom bombing) during your special event. If you need to record the video conference, respect the privacy of the attendees by giving them notice before recording begins. Additionally, participants can use the virtual background feature, when available, if they do not want to have their surroundings visible.
The internet has allowed many Canadians to work remotely over the past year and a half. For AU working from home is soon going to become the norm. This week will be about how to continue working from home safely by keeping security top of mind. Remember, you are the best line of defense against cyber-attacks targeted at AU.
Here are a few tips to ensure that AU remains cyber secure while working from home.
- Always use a secure connection to connect to the AU network and if you are a learner, to your company’s network. You can do this by connecting via a sanctioned Virtual Private Network for the system that you are connecting to.
- Limit the locations that you connect your work system such as your home network and other trusted private networks. Avoid connecting to the AU network or your company’s network with any unsecured public Wi-Fi. When you are in a location outside your trusted locations, it is advisable to use your mobile device as a hotspot rather than connecting to a public Wi-Fi.
- Restrict access to work data and information to your work device. Do not transfer work data and information to home computer or personal devices. There is a risk that personal computers and mobile devices do not have the latest security updates for the operating systems and browsers.
- Ensure that you install all necessary updates as they become available. Make sure your computer has the latest applications, operating systems, network tools, and internal software installed.
- Where applicable, activate and use multi-factor authentication to ensure that no one else can use your credentials to access your work system. Create strong unique passphrases for your laptop, corporate mobile device, and email.
- Maintain a clean desk policy and avoid exposing documents with sensitive information even in your home. Securely store, print and dispose paper documents with sensitive information.
This past year has been a difficult one for many Canadians, but two groups have faced unique challenges: kids (who are missing school, friends, and activities) and small and medium businesses (who had to shift suddenly from business as usual). In this final week of the Cybersecurity Awareness Month, the focus is on how to help kids stay secure on their online interactions. This theme is particularly important because the children are our legacy for the future. Today is the opportunity for us to build the secure tomorrow that we hope for.
Children that are born into a world of tablets and smartphones have an inherent comfort with the Internet that is absent in many adults. This comfort, however, often leads to a blindness about potential risks. With the prevalence of social media platforms and online gaming (especially due to the restrictions that the pandemic has imposed on us all), it is increasingly important to teach kids about secure online interactions. The dangers that kids face today range from cyberbullying, predators, inappropriate content and phishing scams to name a few. The concern for many parents/caregivers today is how do we provide internet safety for our children while respecting individuality in children and exhibiting trust. Here are a few tips.
- One of the easiest ways to ensure children’s safety online is to use parental controls on the child’s device, especially when it comes to downloads. Make sure the kids in your care get permission from you before downloading anything online - if it’s from the official app store on their device. You should always try to download directly from the vendor or use an official website whenever possible to make sure the application is legitimate.
- Cyberbullying is a serious issue that is affecting most kids online. Cyberbullying is using computers, smartphones or other connected devices to embarrass, hurt, mock, threaten or be mean to someone online. The first step that children should take when they have experienced cyberbullying is to block the person and tell an adult that they trust. As adults we should strive to be supportive to the kids.
- Phishing isn’t just for adults. Phishing messages might include offers of prizes in exchange for personal information, links to malware disguised as “free” games or add-on content, requests for personal information disguised in a fun way. telling kids to avoid clicking on links or downloads before you’ve verified them. Children should be made aware of these scams.
- Ensure that children are not sharing too much information. Oversharing can impact our lives in many ways. Oversharing can damage our cyber security by making us the target of phishing scams and malware. Oversharing can also affect our relationships with others for instance sharing pictures of a friend that they don’t want in the public domain. It is important to remind kids that: once you have written something online there is a high possibility that many people have seen it and others might have taken a screenshot.
- Online reputation is how other people see and think of you based on what you say and do online. It’s important for children to maintain a good online reputation (just like their reputation at school or home) as it may affect how people treat them today and in the future.

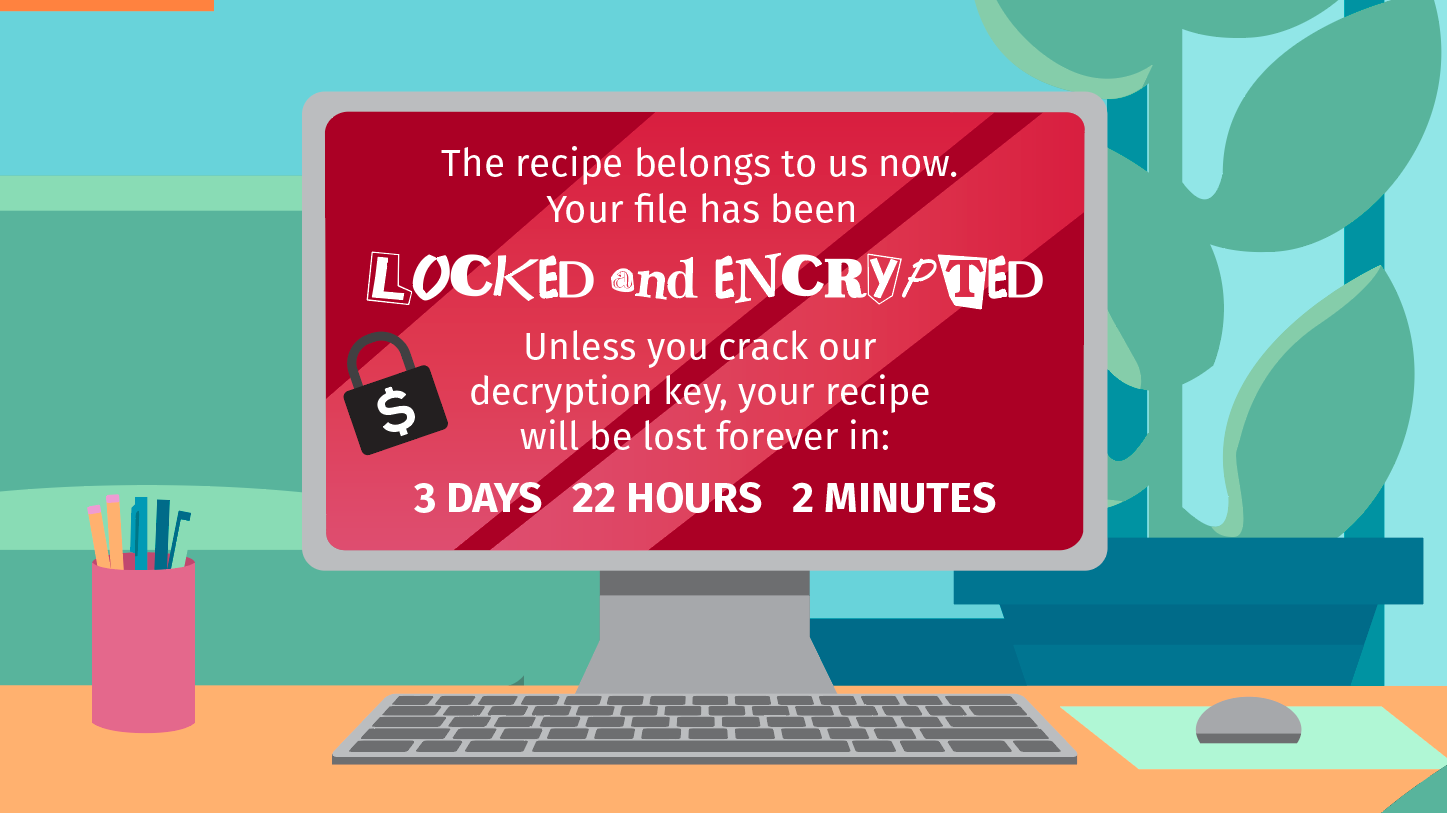 In the first challenge, you'll be in an office setting where they must crack the decryption key for the ransomware and trace where the attack came from by answering clues about security awareness on social media platforms and phishing indicators.
In the first challenge, you'll be in an office setting where they must crack the decryption key for the ransomware and trace where the attack came from by answering clues about security awareness on social media platforms and phishing indicators. From the airport, you will get one step closer to finding the stolen recipe by answering clues about social engineering scams on a dropped cell phone.
From the airport, you will get one step closer to finding the stolen recipe by answering clues about social engineering scams on a dropped cell phone. In a coffee shop, you will need to use a mysterious unattended laptop to answer clues about passphrases and security risks for remote workers.
In a coffee shop, you will need to use a mysterious unattended laptop to answer clues about passphrases and security risks for remote workers. In the fourth and final challenge, you will construct a keypad code by answering clues about securing mobile devices and applications to catch the thieves and solve the mystery.
In the fourth and final challenge, you will construct a keypad code by answering clues about securing mobile devices and applications to catch the thieves and solve the mystery.